POST
Welcome to POST by ResTech Solutions
Thank you for subscribing to our newsletter. Every week we will bring you new content covering recent events and news related to technology, Microsoft, Apple, Google, tips & tricks, useful information, and more! To read the full articles in our newsletters you can either click on the image or article headline. We've had a great response each week to our newsletter and we've been hard at work to bring you even more great information this week. Please let us know what you've enjoyed thus far about our newsletter. To see past issues click on the archives link above.
Why the name POST? In the world of computers POST stands for Power On Self Test. This is the action computers take when they are first powered on to check their basic functionality prior to loading the operating system. We decided to take this same concept and to provide you with useful technology information at the beginning of your week to help get you started. POST is also a term associated with news as well and we felt this was an appropriate and fitting name.
If you have suggestions about topics you are interested in or would like more information on any of the articles presented in our newsletters you can fill out our Content Request form to let us know what you would like to know.
Do you need any help or assistance with any item in our newsletter? Reach out and we will be happy to help.
Reply to this email to let us know what you liked. Please forward this newsletter to anyone who needs this information.
The best thank you that you can give us is by sending us referrals. It means so much to receive a referral. We look forward to having you with us every week! Let's POST and get started with this issue.
News

Windows Malware Steals 26 Million Passwords: How To Check If I’m Affected?
Image from Fossbytes
There has been another major malware event that has stolen 26 million passwords. The malware has affected over 3 million PCs. Where did the data come from?
After the Dominos India data theft, data from a 1.2TB database containing browser autofill data, cookies information, usernames and passwords, and payment information has been taken away by unidentified malware, according to researchers from NordLocker.
The stolen data contained over 2 billion browser cookies, 1.1 million email addresses, 6.6 million files, and over 26 million login credentials. These files also included people’s passwords stored in a text file created using Notepad and 650000 Word and PDF files, and over 1 million images.
We all need to make a habit of clearing our browser cookies and cache, a process that can be automated each time you close the browser. We also need to stop storing passwords in the browser. Browsers are not a safe place to store information as they really are not that protected and data stored is likely not encrypted or has very weak protection that is easily broken/bypassed.
As we have been seeing with more frequency there has been an increase in cybersecurity incidents. We can no longer afford to sit back and think we are immune. NO ONE IS IMMUNE. You can take steps to improve your security and protection. Use a password manager to store all sensitive information such as passwords and notes. Use advanced security protection for your computers, use a VPN, encrypt your computer, etc. Please do something other than the status quo as it no longer works.
Cyber Security

6 Reasons You Shouldn't Use Your Web Browser's Password Manager
Image from MUO
Do you need further proof/evidence as to why storing passwords in your web browser is not secure? This article will tell you why.
When it comes to storing passwords in the browser there is almost no security protecting the passwords. Anyone who knows or can get your computer password and use it to easily access the passwords stored in the browser. There are many other reasons but the security issues alone should be reason enough. You need to be using a stand alone password manager anyway.
5 essential steps to protect your computer from ransomware
Image from Kim Komando
Ransomware has been on a war path recently. Just look at all the headlines in the news. Those are only the incidents that have been reported because they have been major breaches. There are many ransomware attacks that happen everyday and many could have been prevented.
Check out the linked article for 5 simple ways you and protect yourself from malware. Please take action and ask for help if you are unsure of how to protect yourself from malware/ransomware.
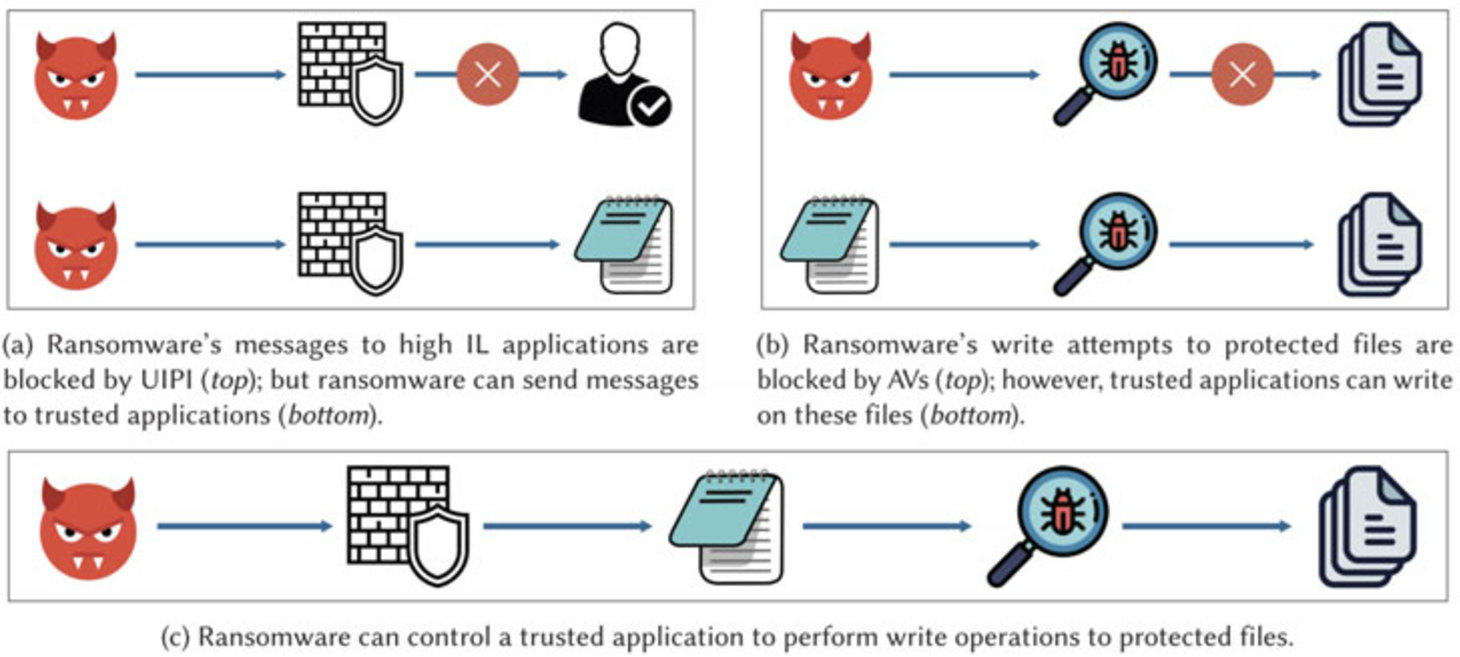
Malware Can Use This Trick to Bypass Ransomware Defense in Antivirus Solutions
Image from The Hacker News
Antivirus solutions alone are no longer good enough to protect against ransomware. AV solutions use a definition based approach to protect a system and their databases are almost always out of date because of how fast new malware/ransomware variants come out.
Many businesses, including ResTech, are adopting a zero-trust model where everything will be denied and only allows applications and processes will be able to run. Couple this with an advanced endpoint protection solutions that uses behavior and AI to assess threats and you will have a much better layer of protection against malware and ransomware.
Windows

Microsoft Brings News and Interests to Every Windows 10 Users Taskbar
Image from MUO
Just within the past week many systems have been receiving this new update from Microsoft. You will see a new icon on your taskbar where you will be able to access your news and interests. While Microsoft enables this new feature by default you can disable it if you wish. To do so you will need to right click on the taskbar from your primary screen (if you have more than one). Move your mouse to News and interests and on the new menu that slides out select Turn off. The new feature will now disappear from your taskbar. Repeat the process to enable it.

7 Tools to Increase Hard Drive Performance on Windows
Image from MUO
If your computer has a hard disk drive installed chances are good that over time you will begin to experience performance issues with the drive. Since these drives are mechanical they will begin to wear out and slow down. By performing some regular maintenance you can keep the performance up and the drives working longer baring any physical issue.
- Clean out temp files
- Defragment the drive - this will recombine data that may have been split on the drive
- Shut down the system when not in use - the more a hard drive runs the sooner it will likely begin to experience issues. Shutting down the system will keep the drive from running and will reduce the wear and tear on it.
Check out the linked article for more details. It is also important to note that some of these tasks, such as defragging, will not be applicable to solid state drive. Ultimately the best option for performance is to upgrade the hard drive to a solid state drive. The data on the hard drive can be cloned to the solid state drive.

How to Capture Video Clips in Windows 10
Image from PCMag
You likely know that you can take a screenshot on your computer and that the process is fairly simple. Just open up the Windows Snipping Tool and capture what you need. What if you need to make a video clip? Well you can do that too using the built in Game Bar in Windows. Check out the linked article for full details.
Tips & Tricks
25 Outlook 2016 Command Line Switches You Have to Know
Image from MUO
As a business user you would usually use Outlook as your email client. Did you know there are many simple commands you can run to accomplish many tasks in Outlook without having to dig through the various menu options? Check out the linked article for some command you should know.
Useful Information

5 Features That Make Plex the Perfect All-In-One Media Streaming Platform
Image from MUO
In case you're not familiar with Plex, it is best described as an all-in-one media streaming and organizing application.
Plex is a great platform to use if you have a lot of your own media content that you want to organize and even stream. Yes, you can create your own personal Netflix like setup using Plex. Plex is worth checking out and it is a platform I have personally been using for years to organize and stream my personal content. There is even a watch together feature where you can invite other Plex users to watch your content with you.
FAQ of the Week

Does HTTPS Protect Data in Transit?
Image from MUO
Each week we will address a frequently asked question. This week we are looking at data in transit over HTTPS.
The short answer is yes, the data is protected in transit over HTTPS. Other methods such as SSL/TLS provide encryption in transit. Just because you see an HTTPS enabled site does not guarantee full protection. Cyber criminals are getting crafty and can find ways around the protection.
I highly recommend that you read the linked article for full details. I know you may come away with more questions so I do encourage you to follow up if you have additional questions.
